Overview
Ethical Hacking is one of the mainstream words that has created a buzz in the present world. By now, almost everyone would have come across the term "Ethical Hacking", however, only a few of them know what Ethical Hacking is all about. A predominant of people assume that the word "hacking" denotes something illegal. Here in this Hacking Tutorial session, we will drive you deep into the Ethical Hacking concepts that will aid you to enhance your knowledge on Ethical Hacking concepts and the other important topics that are associated with it such as Computer network security, Computer Systems and, Hardware.
Intended Audience
This Ethical Hacking Tutorial session has been curated with the purpose for those who are seeking to learn the Ethical Hacking concepts for equipping their knowledge with the Ethical Hacking concepts and those who are planning to head-start their career in the Cyber Security domain.
Prerequisites
It is preferable to have an in-depth understanding of the Computer basics that will aid you to comprehend the hacking concepts at ease.Hacking is one of the important aspects of computing for more than a decade and this is one of the wider disciplines that conceals topics of a broader range. Initially, the very first event of hacking took place at MIT in the year 1960, and therein the word " Hacker" was created.
Hacking is nothing but the method of identifying the feasible entry points that are present in the computer system or network and decisively stepping into them. Hacking is generally performed for obtaining unauthorized access from the computer system or network that causes a threat to the system for stealing the highly confidential information that is found in the computer system.
The term Hacking is legal as long as it is performed for identifying the weakness in the network system or the computer for the purpose of testing. And this is what is called "Ethical Hacking". The techy experts who perform the act of hacking are termed as "Hacker". The Hackers are those who gain knowledge for comprehending how the system operates, how it is being developed, and the endeavors to play with the system.
Hacking is the method of identifying the threats in the system and turning those threats as the entry card for penetrating into the system, to execute malicious activities like stealing or deleting the confidential information that is stored in the device. As mentioned earlier hacking is often considered illegal that drives you to chaos and extreme consequences when you are caught red-handed. Also, there are people who have been convicted and sentenced to years of imprisonment for the act of hacking.
However, acting is termed as legal when it is performed with the required permission. Usually, the companies recruit Computer Experts into their organization for hacking into their systems for finding out the weak endpoints and the vulnerabilities that could be fixed. It is performed as a precautionary step to protect the confidential details of an organization against malicious hackers. The people who hack into the system with the permission of higher authorities are called Ethical Hackers. Ethical Hacking Course in Chennai at FITA Academy trains you efficiently on the hacking and security concepts under the mentorship of Certified Ethical Hackers with hands-on training practices.
Kinds of Hacking
Now, let is see in-depth the different kinds of Hacking and categorize them based on how it is being performed.
- Network Hacking - It is the process of obtaining information of any Network using tools such as Ping, Tracert, NS Lookup, NetStat, and Telnet. Networking hacking is usually performed with the intent to cause a threat to the Network system and hinder the operations of the network.
- Website Hacking - Website Hacking is an act of getting unauthorized control over the Web Server and this is related to software like interfaces and databases.
- Email Hacking - This is the act of obtaining unauthorized access to the Email account and this is executed without any consent of the owner.
- Password Hacking - It is the method of mending the secret passwords from the data that are either transmitted or stored by the computer system.
- Ethical Hacking - Ethical Hacking includes the act of identifying the flaws in the network or computer system for testing purposes and this finally gets fixed.
- Computer Hacking - It is the act of stealing the Computer ID and the Password using hacking methods and gaining unauthorized access to the computer system.
Benefits of Hacking
Hacking is more useful in the below circumstances,
- For recovering the lost information, in case you had lost your password.
- Having the Computer Systems that forbids the malicious hackers from obtaining the access.
- For executing the penetration testing to intensify the network and computer security.
- To place more preventative measures at the place for protecting the security breaches.
Downsides of Hacking
- Hacking is perilous if you do it with harmful intentions. This shall create Privacy Violation.
- Immense Security Breach.
- Hindrances in the System operations.
- Rejection of Service attacks.
- Malicious threats to the system.
- Unauthorized access to the system or the private information.
Why is Hacking performed?
The purpose to perform Hacking may differ according to the individual's intentions. Here is the list of reasons,
- Money extortion
- For Fun
- To Show-off
- Stealing confidential information
- To hamper the privacy
- To damage the System functioning
- To test the security of the system
- Also, to break-down the policy compliance
What is Hacking?
The process of Hacking is termed as the method of identifying the set of vulnerabilities on the target system and exploiting them systematically. Ethical Hacking is the field that ascertains itself from hacking by adding the important elements to a process - 'consent'. The inclusion of the term 'consent' to this process helps in attaining two objectives and they are-
- The Process eventually becomes a legal activity.
- The Ethical Hacker seeks permission before hacking into a system but this is done because it should be ensured that the hacking is performed legally and the hacker doesn't have any malicious intent. They usually do this to make the hacker bind to a work legally and enhance the security systems of the company.
The Roles of the Ethical Hackers
Ethical Hackers have different roles in the organization for which they work for. Taking the fact that an Ethical Hacker is hired by both the Public and Private concerns for alike reasons, however, the end goals may differ and be diverse, and so, the hackers are appointed for the below attributes,
- An Ethical Hacker predominantly works for protecting the privacy of the organization they work for.
- These Hackers should flawlessly report any kind of discrepancies in the system to the respective division in correspondence to rectifying the vulnerability.
- Also, they should update the Software and Hardware vendor in concern with any vulnerabilities that are identified in the product which are used for executing the business operations.
Importance of Ethical Hacking
We all know that Data is the lifeline of the business and it has turned out to be a precious resource for the business. Further, the preservation of the integrity and privacy of the data has also grown profound in the present age.
Inherently, this makes Ethical Hacking the most important thing in the present. It is because of the fact that every business around the globe now functions primarily on the internet or the cloud platform. For that reason be it a Public Relations Corporations or the Digital Marketing medium everything functions on the online platform with the help of internet services today. Consequently, it mandated the need for hackers who can protect the security consoles of the organizations.
Moreover, the Hackers of the present time have proved themselves to be the best of expertise when it comes to penetrating the system. In the recent past, hacking has caused massive losses that account for more than a million dollars in most organizations. These incidents have exhorted businesses across the globe to reconsider their stance in the market and it eventually emphasized the significance of Cyber Security and Ethical Hacking Course in Trichy, as professionals seek the right training to protect digital assets and prevent cyber threats effectively.
Security Threats
Having seen What an Ethical Hacker does and the importance of the Hacker in the organization. Now let us further dive deep into the major elements of Ethical hacking in this hacking tutorial.
Security Threats
In case if you are a professional Ethical Hacker, then your day-to-day activities include managing the cluster of security threats. The Threats that have the attribute to harm a specific system or the major console of the organization as a whole. So let us go through the different kinds of security threats that take place in an organization.
Generally, the threats shall be classified into two major categories and they are,
- Physical Threats.
- Non- Physical Threats.
Physical Threats
The Physical threats are further classified into three different categories and they are
- External - Fire explosion, Floods, and Earthquakes
- Internal - Faulty Power Supply, Internal Hardware failures, and Hardware error or fire,
- Human - Human beings can also cause a threat and they are accidental errors, arson, and vandalism.
Non - Physical threats
These are the threats that consist of all the threats that have no physical manifestation. These kinds of threats are also called logical threats. The below diagram neatly depicts the usual non-physical threats:
Ethical Hackers usually operate with non-physical threats on a daily basis, and it is the work of an Ethical Hacker to overcome these threats with required preventive measures.
Preventive Measures of Security Threats
Usually, the preventive measures that are embraced by the Ethical Hackers pretense to vary according to the organization, and to the situation, they have encountered. However, below are some of the important methods that are followed ubiquitously,
- The Authentication system shall be enhanced and it is made more efficient to use the multi-factor authentication system. The Authentication methods could be in different forms and they are the smart cards, captchas, biometrics, passwords, user IDs.
- All organizations should have the proper logical security measures in place. It includes the cognitive cybersecurity measures that are affiliated with the organization that functions on the incident response system.
- Prevention Systems/ Intrusion-detection system shall be used for safeguarding the disapproval of the service attacks. There are various other measures that can be used for ignoring the rejection of service attacks.
- To protect the system against the entities such as trojans, viruses, and worms the organizations may at times make use of the distinctly designed anti-viruses that are developed for accomplishing the needs of the company. Furthermore, the organizations can also identify its benefits for using the control measures and on how to use the external storage devices, and visiting a website that is likely to download the unauthorized programs into the targeted computer.
Types of Hackers
In this Ethical Hacking Tutorial session, we are initially going to see who are hackers and a brief description of the different kinds of Hackers.
Firstly, let us understand Who are the Hackers?
Hackers are the people that are associated with Computers and they like to dabble with any electronic items, systems, or software. Hackers are those who fancy penetrating a system for discovering its operation and identifying the different ways to handle it - technically, electronically, and mechanically. To sum up the above things, Hackers are the developers or techy experts who contribute real-time solutions and ideas to face an issue. Below are the different kinds of Hackers in the discipline of Computer Science.
- White Hat Hackers
- Black Hat Hackers
- Grey Hat Hackers
- Hired Hackers
- Script Kiddies
- Elite Hackers
- Spy Hackers
White Hat Hackers
These are the Hackers who perform the Hacking activities with good intent. Usually, these Hackers are Computer Security Experts who are specialists in penetration testing and other technical knacks to ensure the safety of the organizations. These Hackers are the professionals who constantly defend the growing technology to fight the criminally-minded hackers.
Black Hat Hackers
These are the Hackers who are also known as Crackers who perform the hacking activity with the intent of obtaining unauthorized access to the system and causing a threat to its operation for stealing confidential information. These Hackers technically out the place the White Hat Hackers. Black Hat Hackers are always considered illegal because of their malicious intent. These Hackers invade into a system or network for stealing information or money. Also, these Hackers can send Spam emails by using your server to any email address for the self or particular brand's promotion. A Black Hat Hacker is a person behind the computer who aims to find the vulnerability in your networks or computer and they break into it.
Grey Hat Hackers
These are the hackers who have the blend of both the White and Black hat hackers. The Grey Hat hackers usually surf into the internet for looking at vulnerable threats in the System, Networks, Phone system, or Computers. Once they identify the vulnerability, then they shall hack into them and fix it. Later they inform the System Administrator what they do and charge a small fee for identifying the threat and fixing it. And so these Hackers are also called the White Hat Hackers in this perspective. The important thing to be noted here is that they can also perform all these hacking activities without the consent of the owner of a computer, network, or website, and in this aspect, they are termed as the Black Hat Hackers.
Script Kiddies
This is the defaming phrase for the Black Hat Hackers. These are the hackers who don't possess more knowledge of the hacking. Rather, they use them as the readymade tools that are used for breaking into the network or computer. These are the Hackers who have less or no knowledge of programming or they execute the hacking for fame or fun.
Hired Hackers
These are the Hackers who are specifically recruited for controlling Cyberspace and defending a nation from cyber-warfare crime. The prime motto is to protect the nation's confidential information with utmost care.
Elite Hackers
They are considered as the Masters of all types of Hacking. These Hackers usually have a good reputation and fame when compared with the other types of Hackers. These Hackers are treated as Senior-level hackers in the hacking community. They are also called the Masters of Hacking and deception.
Spy Hackers
These types of hackers are generally recruited mostly in corporations for infiltrating the business secrets, trading, and competition. The Spy Hackers use the same tactics as that of the hacktivist however the motto of these hackers is to meet the goal of the client and complete the assigned task. Learning about such hacker types and their motives is an important part of an Ethical Hacking Course in Erode, which helps students understand real-world cyber threats and defense techniques.
Terminologies used in Ethical Hacking
In this Ethical Hacking Tutorial tips and tricks, we have enlisted some of the important terminologies that are predominantly used in the domain of the hacking field.
- Attack - The Attack is the action that is performed on the system for gaining access and infuses the sensitive data.
- Adware - It is the Software that is curated for pushing the pre-chosen ads to be displayed on your system.
- Bot - The Bot is the program that optimizes the action so it shall be performed often at a higher frequency rate and for the sustained duration when compared to the human operator. For instance, sending the FTP, Telnet, and HTTP at a higher rate or while calling the script for building the objects at a higher rate.
- Back Door - A back door is also known as the ‘trap door’, which is the hidden entry for computing the software or device that detours the security measures like logins & password protections.
- Botnet - The Botnet is also called the ‘Zombie Army’, and it is the set of computers that are controlled and operated without the knowledge of the owners. Usually, the Botnets are used for sending the make denial or the spam service attacks.
- Buffer Overflow - It is the flaw that takes place when there is more data that is written on the block of the memory or on the buffer itself that is allowed to hold.
- Brute Force Attacks - The Brute Force attack is the simplest and automated kind of method for obtaining access from the system or the website. This tries a various combination of passwords, usernames, again and again until this steps in.
- Cracker - The Cracker is the one that changes the software for accessing the features that are considered to be objectionable by a person for cracking the software mainly for copying the protection features.
- Clone Phishing - A Clone Phishing is the alteration of the existing legitimate email with the false link and the trick of the recipient for providing the personal information.
- DDoS - It is the Distributed denial of service attack.
- Denial of the Service attack (DoS) - The denial of the service attack is the malicious pursuit for making the network resource or the server unavailable for the users, generally by disrupting or suspending the services of the hosted connection of the Internet.
- Exploit - The Exploit is the kind of software, a sequence of commands, or chunk of data that takes the benefits of the vulnerability or the bug for concessioning the security of the network system or the computer.
- Exploit Kit - The Exploit Kit is the software system that is curated for running the Web servers with the intent of finding the vulnerabilities of the software on the client's machine for exploiting the identified vulnerabilities and communicating with it for executing and uploading the codes of the client.
- Firewall - The Firewall is the filter that is blueprinted in a manner to prohibit unwanted intruders besides the network or the computer systems and the users who are inside the firewall.
- Logic Bomb - The Virus that is stashed into the system that provokes the malicious action where few conditions are met. The general version of this is called a time bomb.
- Keystroke Logging - It is the method of tracking the keys that are found in the computer. This is simply the map of the human interface/computer. This is predominantly used by the Black and Gray hat hackers for recording the login IDs and the Passwords. The Keyloggers generally stash into the device using the Trojan that is deposited by the phishing mail.
- Master Program - The Master Program is a program that a Black Hat hacker makes use of it for the remote transmission of the commands and the infected zombie drones to bear the Denial of the Service attacks or the spam attacks.
- Malware - Malware is the canopy that is used for referring to the different forms of intrusive or hostile software that includes worms, computer viruses, Trojan horses, Spyware, Ransomware, Scareware, Adware, and other malicious programs.
- Phishing - It is the e-mail fraud method on which the perpetrator pushes out the legitimate-looking email in an attempt to obtain financial and personal information from the recipients.
- Phreaker - They are termed as the original computer hackers and they are the ones who crack into a telephone network illicitly for tapping the phone line or the free long-distance phone calls.
- Rootkit - It is the Stealthy kind of software, which is malicious, and this is designed for hiding the existence of a few programs or processes from the normal methods for finding and enabling the extended privilege of access to the computer.
- Shrink Wrap Code - The Code attack is the method of exploiting holes in poorly designed or updated software.
- Spam - Spam is generally the unsolicited email that is also called junk mail that is sent to a vast number of recipients without their assent.
- Spoofing - It is the method that is used for obtaining unauthorized access to the computers, by which the intruder forwards the message to the computer with the IP address and it denotes that the text is coming from the trusted host.
- Social Engineering - Social Engineering signifies entrapping someone with the intent to gain personal and sensitive information such as User name passwords and Credit card details.
- SQL Injection - SQL injection is the code injection technique that is used for attacking the data-driven applications on which the malicious SQL statements are affixed to the entry field to execute.
- Spyware - It is the software that functions with the purpose to obtain information regarding the organization or person without their assent. Also, this Spyware can send the details to the other entity without the consent of the consumers or that they defend the control of the computer without the idea of the consumers.
- Trojan - The Trojan or a Trojan Horse is one of the malicious programs that are masked to be like valid programs to make it harder for differentiating them from the programs which are meant to be designed in the aspect alter the information, destroy files, or steal the passwords or pieces of information.
- Threat - A threat is a possible danger that shall exploit the vulnerability or the bug for encompassing the security of the network system or computer.
- Vulnerability - Vulnerability is the Weakness that permits the hacker to constitute the security of the network or computer system.
- Virus - The Virus is the malicious code or program that can copy typically itself and has the determined effect like destroying data or corrupting the system.
- Cross-site Scripting - Cross-site scripting is the kind of computer security that has the vulnerability that is mostly found on Web applications. The XSS allows the attackers to infuse the client-side script on a Web page that can also be seen by other users.
- Worms - A worm is a self-replicating virus that shall not alter the files however this resides on the active memory and then duplicates itself.
- Zombie Drone - It is also called a hi-jacked computer which shall be used unanimously as the 'drone' or 'soldier' for performing malicious activities like unwanted spam emails.
Ethical Hacking Tools
In this Hacking tutorial module, we have discussed the different Ethical Hacking tools that are used broadly by the users for preventing hacking and protecting the network system of the organization. Some of the important Ethical Hacking tools are as follows,
- Metasploit
- NMAP
- Burp Suite
- Cain & Abel
- Angry IP Scanner
- Ether Peek
- Ettercap
- QualysGuard
- SuperScan
- LC4
- Web Inspect
- Tone LOC
- Network Stumbler
- LANguard Network Security Scanner
Metasploit
It is deemed to be one of the powerful exploit tools. This is a product of the Rapid7 and the predominant of its resources are found @ www.metasploit.com. Also, the Metasploit comes in two different versions and they are free edition and commercial. The Metasploit shall be used with the Web UI or the Command prompt. With the Metasploit tool, you can execute the following operations:
- Identify the Network or you can import the scanned data.
- Conduct the fundamental penetration tests on the small networks.
- You can rush the spot checks on exploitability of vulnerabilities.
- It is possible to Browse the exploit modules and later run the single exploits on the hosts.
NMAP
The acronym NMAP stands for Network Mapper. It is an open-source tool that is primarily used for networking and security auditing. The map was initially designed for scanning larger networks however this shall equally function better for the single hosts. This is also useful for the Network Administrators for the tasks like managing service, upgrading schedules, network inventory, and tracking the host and the service uptime.
The Nmap make use of the raw IP Packets for determining the
- What are the different hosts that are found on the Network?
- The Services that the hosts are providing
- The types of firewalls that are in use and the other types of characteristics.
The Nmap generally runs on all the important operating systems like Windows, Linux, OS X, and Mac.
Burp Suite
The Burp Suite is a famous platform that is used broadly for executing the security testing of Web Applications. It consists of different tools that function in association with the support for the complete testing process, right from the beginning of the analysis and mapping of the application's attack area, via finding and attacking the security of the computer system and network.
The Burp is simple to use and it enables the administrators to have full control for merging the advanced manual techniques with the automation to perform efficient testing. A Burp shall be configured easily and that it consists of the feature that can even assist the skilled testers with their job.
Cain & Abel
It is the password recovery tool that is used for recovering the tool for the Microsoft Operating Systems. This helps in faster recovery of different kinds of passwords by deploying any of the below methods:
- Revealing password boxes
- Recovering wireless network keys.
- Network Sniffing.
- Documenting the VoIP conversations.
- Breach the encrypted passwords by applying the Brute-force, Dictionary, and Cryptanalysis attacks.
- Uncovering the cached passwords and finding the routing protocols.
Cain and Abel are some of the useful tools that are used by professional penetration testers, hackers, and security consultants.
Angry IP Scanner
The Angry IP scanner is one of the lightweight and cross-platform of the IP port and address scanner. It is capable of scanning the IP addresses of any range. This shall also be freely used and copied anywhere.
To enhance the pace of scanning, you can use the multi-threaded approach, where the detached scanning thread is built for all the scanned IP addresses. The Angry IP Scanner shall easily clink the IP addresses for checking whether it is awake, later it solves the hostname that identifies the scanned ports and MAC address. The total amount of the collected data for all hosts shall be saved to the XML, CSV, IP-Port List files, or TXT. With the support of the Plugins, the Angry IP Scanner can obtain all information of the scanned IPs./p>
EtherPeek
It is the best tool that streamlines the network analysis in the multiprotocol diverse network environment. This is the smallest tool that shall be easily installed in just a few minutes.
It anxiously sniffs the traffic to the packets on the network. The EtherPeek by default supports the protocols like IP Address Resolution Protocol, AppleTalk, IP, NetWare, UDP, TCP, NBT packets, and NetBEUI.
QualysGuard
It is one of the combined suites of the tools that shall be used for reducing the security operations and also the compliance cost. It distributes the critical security intelligence that is demanded highly and also it automates the entire cycle of compliance, auditing, web applications, and protection of the IT systems. It consists of a set of tools that can detect, handle and protect the global network.
SuperScan
It is one of the robust tools that is used for the administration of networks to scan the TCP ports and solve the hostnames. This is a user-friendly interface with which you can perform the below activities,
- Designate the custom helper application in any of the ports.
- Change the port list and description by using the built-in editor.
- You will be able to see the responses from the connected hosts.
- You can execute the ping scan and the ports to scan using the IP range.
- It is easy to bridge with any of the discovered open ports.
- Blend the port lists for building the new ones.
- It shall scan any port of range from the built-in list or the given range.
LC4
It was earlier called the LOphtCrack. This is an application that is predominantly used for auditing and recovering the application. Also, this tool is used for testing the strength of the password and at the time you can restore the lost passwords of Microsoft Windows by applying any of the following hybrid attacks, brute-force, and dictionary.
It restores the Windows User Account passwords for assigning the migration of users to the other authentic system to access the accounts and passwords for the lost ones.
WebInspect
It is the security assessment tool of the Web Application that supports the detection of vulnerabilities that are known and unknown within a layer of the Web Application.
Also, it helps in checking whether the Web Server is installed properly and it aims to find the common web attacks like directory traversal, parameter injection, and cross-site scripting.
ToneLoc
It is also known as the Tone Locator. It is the most common war dialing computer program i.e written for the MS-DOS at the beginning of the '90s.
It is the method that utilizes the modem to scan the set of telephone numbers immediately, by dialing all the numbers that are found on the local area code.
The Malicious Hackers use the results that are listed on the breaching the security of the computer - to identify the user accounts or finding the modems that shall provide the entry-point to the computer and the other electronic systems. It could also be used by the security personnel for finding the unauthorized devices of the company's telephone directory.
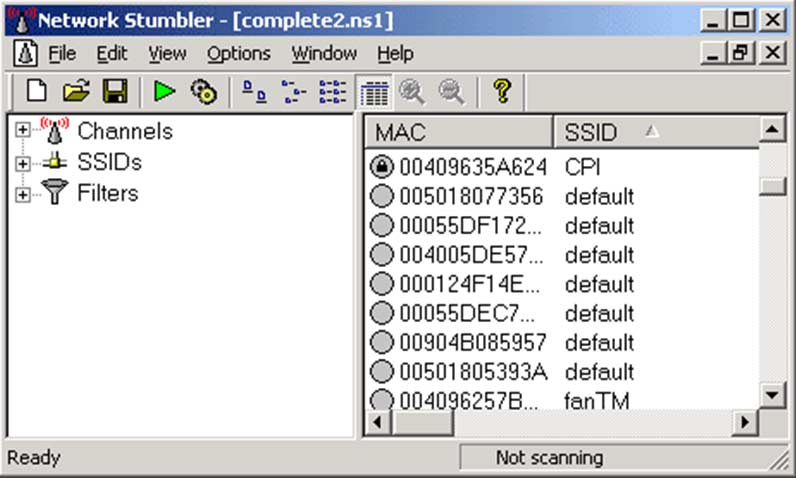
Network Stumbler
It is the WiFi Scanner and also the monitoring tool to the Windows as well. It permits the network professionals to find the WLANs. It is broadly used by hackers and networking enthusiasts as it aids them to determine the non-broadcasting and wireless networks.
The Network Stumbler shall be used to check whether the network is configured properly and whether the coverage and signal strength are proper. Also, this tool is used for determining the interference between more than one wireless network. This tool is also used for non-authorized connections.
LANguard Network Security Scanner
It checks the network on scanning the connected machines that give information about all the nodes. You can also gain information on all the operating systems that are individual. You can determine the registry issues that have the report which is configured in the HTML format. For all the computers, you can enlist the Mac address, Current logged-on user, and the NetBIOS name table.
Ethical Hacking Online Training at FITA Academy comprehends the Hacking concepts along with its tools under the guidance of real-time Ethical Hacking professionals and they help you to clear global certification exams.
Ethical Hacking - Process
Just like other processes, Ethical Hacking also has a set of phases that help the hackers to make the constructed Ethical Hacking attacks. In this Ethical Hacking tutorial let us see the hacking process.
Below are the six predefined phrases of the Ethical Hacking process,
- Reconnaissance
- Scanning
- Gaining Access
- Maintaining Access
- Cleaning Tracks
- Reporting
- Quick Tips
Reconnaissance
In this phase, the attacker obtains the information of the target using the active or passive methods. The tools that are broadly used in this phase are NMAP, Google Dorks, Hping, and Maltego.
Scanning
In this stage, the attacker starts to earnestly probe into the target network or machine for searching the vulnerabilities that shall be exploited. A tool that is utilized in this process is called NMAP, Nexpose, and Nessus.
Gaining Access
At this stage, the vulnerability is identified and you can bid to exploit the complete order into the system. The fundamental tool that is used in this method is called Metasploit.
Maintaining Access
It is the stage where a hacker has obtained access already to a system. Once, when you have obtained the access, the hacker shall configure some of the backdoors to invade into a system, where the needs are accessed in its system for the future. For this process, the Metasploit tool is highly preferred.
Clearing Tracks
It is the process that is in reality an unethical activity. It should be done with the deletion of logos of all the activities that occur at the time of a hacking process.
Reporting
It is the final step of the Ethical hacking process. In this stage, the Ethical Hacker collects the report that is within the findings also they clearly list down the list of findings, tools utilized and the vulnerabilities that are found in the process are explained here.
Quick Tip
Though, this step is not the standard one. You can use this for the various set of tools and processes with adherence to the techniques you are comfortable with. Furthermore, this process is not more important as far as you are capable of achieving the needed results.
Information Gathering Techniques
Obtaining the information is the initial step where the hacker aims to gather the details of the target. Also, over here the hacker uses various sources for gathering information, and those sources are explained briefly in this Hacking tutorial session.
First, let us have a better understanding of What Information Gathering is about?
It is the method of collecting various types of information against the specific system or the victim. Also, we can confidently tell that this is the first stage of the Ethical Hacking Process, where the White and Black hat hackers execute this step. And this is the most crucial step that has to be performed. The more you collect the details of the target, the higher the chances of getting the desired results. Over here the important thing to be noted is that the “Information gathering is not a stage of security testing, but it is the complete art that all penetration testers should master”. There are different techniques, tools, and websites that consist of public sources like Whois and nslookup that aid the hackers to get the information. It is an important step that enables you to get information like (age, phone number, best friend details, DOB, favorite colors, places, books, and much more) to guess the correct password while executing the attack on any of the targets.
Obtaining the information are classified into three different categories and they are,
- Foot Printing
- Scanning
- Enumeration
Foot Printing
Foot Printing is the step of the reconnaissance process that is used for collecting the possible information of the targeted system or network. The Footprinting shall be both active and passive. Checking the company's Website is the best example of passive footprinting where you try to obtain access to sensitive details via social engineering and this is the example of active information collection. This is the step where the hacker tries to obtain the information as much as possible to intrude into the target system or must be able to decide what kind of attacks is applicable for the target.
At this phase, the hacker shall gather the below pieces of information:
- Domain name
- IP Address
- Namespaces
- Phone numbers
- E-mails
- Employees information
- Job Information
In this Ethical hacking basics, we have explained how to extract the fundamental details and easy information that is accessible on any of the network or computer systems that are linked to the Internet.
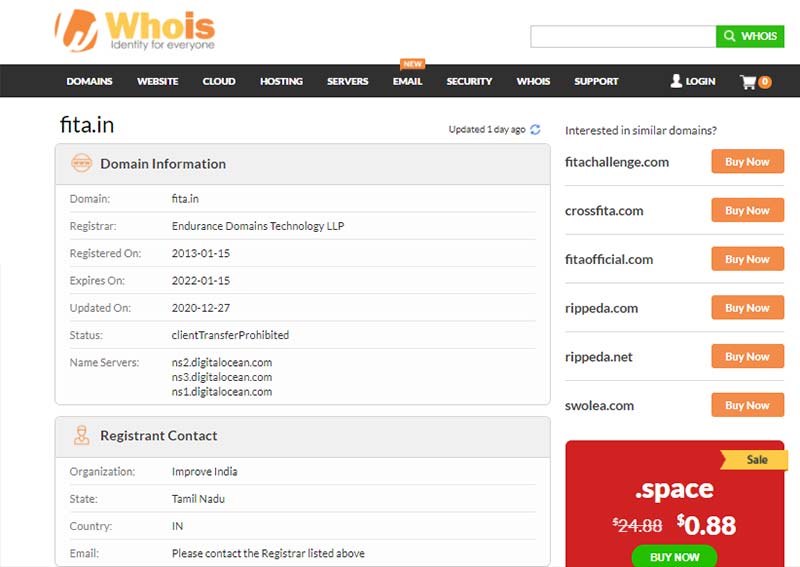
Domain Name information
You can use the http://www.whois.com/whois website for getting the in-depth details of the domain name along with its owner, registrar, expiry, date of registration, owner's contact information, and the name server.
Ethical Hacking Tips and Tricks
It is always advisable to keep the profile of your domain name private and the one that should hide the above details hidden from potential hackers.
Finding IP Address
You can make use of the ping command in your prompt. This command is also found on the Windows and Linux OS. Below is the example that enables you to identify the IP address
IP Address Range
A Small site shall have only one IP address that is related to them, however, the larger websites generally have numerous IP addresses to serve various domains & sub-domains.
You can gain the range of the IP address that is designated to the specific company by using ARIN that is the American Registry for Internet Numbers.
You can type the company's name on the search box for finding out the set of authorized IP addresses for that specific company.
Discovering the Host Company
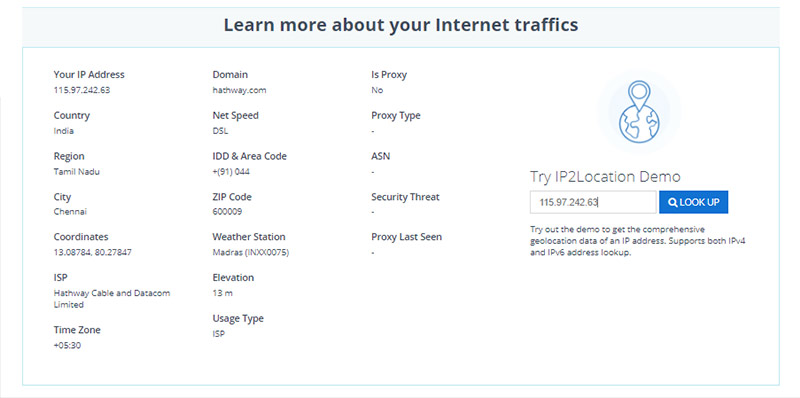
When you have a Website address, you can obtain other details by using the ip2location.com website. Given below is the example that helps you to identify the details of the IP address:
Over here, the ISP row provides you the information of the hosting company as the IP addresses are generally provided by the respective hosting companies.
Ethical Hacking Tips and Tricks
When the Network or the Computer system is linked to the Internet directly, then it is impossible to hide the IP address and the other associated details like location, hosting, ISP. When you have a server that consists of sensitive data, it is advisable to keep the data behind the secure proxy so the hackers need not to obtain the exact information of the actual server. It is a method that is perilous for a potential hacker to crack the access to the server directly. There is also an alternative way through which you can hide the system IP and immediately obtain all the information that is related via Virtual Private Network. When you configure the VPN, then the full traffic routes via a VPN network, so the correct IP address is assigned to your ISP is kept hidden always.
History of a Website
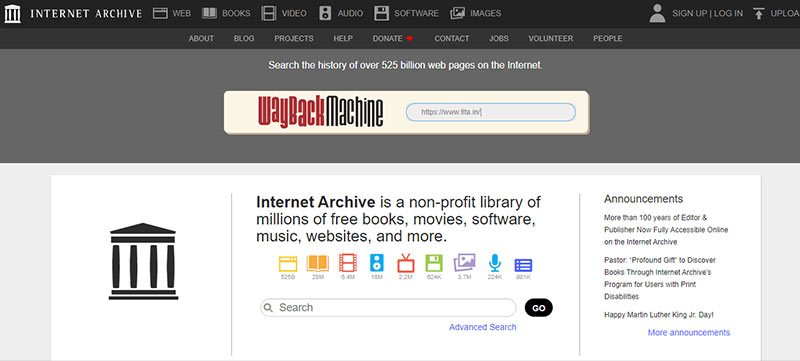
It is easy to find the entire history of the Website using www.archive.org.
You can type the domain name on the search box for identifying how the website looks at a particular time and what are the pages that are found on a website for different dates.
Ethical Hacking Tips and Tricks
Though there are some advantages of keeping your website in an archive database, if you do not prefer to see how your website is processed via different stages, then it is possible to request archive.org to expunge the history of your website.
The other types of Footprinting are as follows
- Network-based Footprinting
- Open-Source Footprinting
- DNS Interrogation
Network-based Footprinting
By using this Footprinting type, the hacker can obtain information like network services, name, shared data with the individuals, data within the group, and user name.
Open-Source Footprinting
It is the kind of footprinting that is safer for possessing all the legal limitations and the hackers can also perform that without any fear as it is termed to be illegal and yet this is coined with the phrase Open-Source. For instance, it includes the following and they are identifying the Email address of someone, scanning the IP via the automated tools, phone number, DOB, the search of the specific person's age, and house address. Most of these companies give the details of the company on their respective official website without the realization of the fact that hackers could benefit from the information given by them.
DNS Interrogation
Once you have collected the information required from the different sectors, using different techniques, a hacker generally requests the DNS using the pre-existing tools. More freeware tools are found on the Online platform to perform the DNS interrogation.
Tricks, Techniques, and Tools used for the Information Gathering
Tricks
You can obtain the details from resources like Social Networking sites i.e Twitter, Facebook, LinkedIn, and much more. These are the sites where the users normally share their data and other details that are associated with them. In fact, the Search Engine occupies a major role in the information collection process. The Hackers shall also get information from different financial services of the specific company like the company's total share, competitor details, market value, and company profile.
The Hackers can also gather information from the email header like
- Sender's Email server
- Address from where the messages were sent
- Sender's IP address
- Sender's Complete name
- Time and Data received from the email server of the originator.
- The Sender's mail server utilizes the authentication system.
Techniques
- OS Identification - It includes sending illicit ICMP or TCP packets for the victim's system to find the OS that is used by a victim on the computer or server.
- Ping sweep technique - This is the type of creating the range of IP addresses that tracks the hackers to the live hosts. Zenmap, ICMPEnum, Nmap, and Fping are few tools that are utilized for pinging more the IP addresses in a single time for generating the set of hosts for the large subnets.
Ethical Hacking Tools used for Information Gathering
- Whois - This is one of the reputed Internet Record listing tools that is used for finding who owns the domain or who saves the specific domain with the contact information. The Internet Corporate of the Assigned Names and Numbers shall regulate the domain ownership and registration details. The records of the Whois have been stated to be exemplarily beneficial and it has developed as a vital resource for handling the website ownership process and domain name registration.
- Metagoofil - It is the other footprinting tool that is used for getting data or information that is found on the internet publicly and also on the internet belonging to a company.
- Harvester - It is the information-gathering tool that is used for obtaining the subdomain or the email address of the specific target. It is the code that is used by the simple Python Script that searches information from the big search engines such as Google, Bing, and Yahoo.
- Netifera - It is one of the efficient tools that provide the entire platform for collecting details of the specific website which you want to attack. It is one of the free tools that are inbuilt with the Backtrack Linux OS. It is the software that provides details like IP address, the total number of Websites hosted, languages used in the Website development, and DNS.
Objectives of Footprinting
- Collect System Information - It consists of the following like system banners, group names, SNMP information, routing tables, system architecture, remote system type, operating system used, passwords, routing protocols, and username.
- Collect Network Information - It gathers information like Domain name, Access Control Mechanism, Internal Domain names, Protocols used, Analog, Existing VPNs, IP addresses for the reachable systems, system enumeration, digital telephones, and authentication mechanisms.
- Gather's Organization's Information - It collects details like Employee details, local details, organization's website, address & phone number, company directory, security policies implemented, web server links, comments in the HTML Source code of the website organizations, press release, and news articles.
Counter Measures
- It explains the kind of information that is required to be placed on the public platform.
- It is advisable not to keep the personal contact number on any of the organization or company phone book that is associated to prevent the war-dialing.
- It is not needed to place the information of any website, social networking account, and profile.
Countermeasures Against the DNS Interrogations
- It disables and restricts the zone transfer of the authorized servers.
- It maintains the External and the Internal DNS separately.
Ethical Hacking - Sniffing
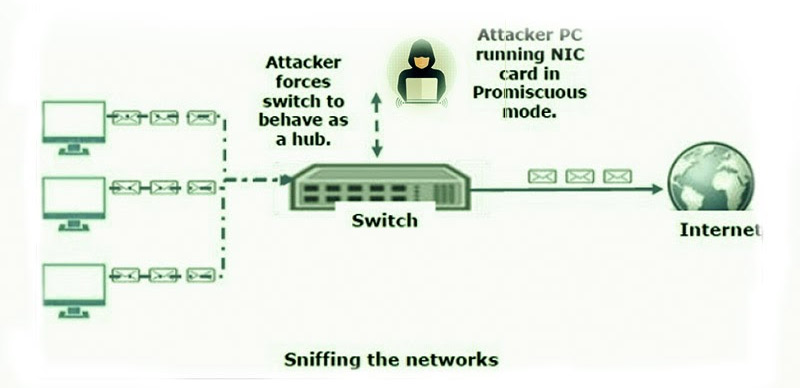
It is the method of capturing and handling all packets that pass via a specific network using the sniffing tools. This is the method of "tapping phone wires" to know the details of the conversation. This is also called the wiretapping that is applied to computer networks.
There are many possibilities when the group of enterprises switches the ports that are open and then the one which the employees could sniff the complete traffic of a network. Anyone on the same location shall also plug into the network using the wifi or the Ethernet cable to sniff the complete traffic.
Also, Sniffing permits you to see all kinds of traffic that are both unprotected and protected. On the right conditions with the right set of protocols in the place, attacking the party shall be able to get the information that is used for other attacks or for issuing the other network issues. In this hacking tutorial module, we can see what are the things that could be sniffed,
Below are the things that can be sniffed
- Email traffic
- FTP passwords
- Web traffics
- Telnet passwords
- Router configuration
- Chat sessions
- DNS traffic
Work Process of Sniffing
Usually, the Sniffer makes the NIC of a system to a promiscuous mode so you can follow all the data that are transmitted in this session. The Promiscuous mode denotes the distinct method of Ethernet hardware, in the specific Network Interface Cards, that permits the NIC to accept all the traffic on a network, though it is not remitted to this NIC.
The default feature of the NIC is that it avoids the traffic that is not remitted to it and this is performed by analyzing the terminal address of an Ethernet packet that is within a hardware address of a device. Though this sounds like a proper method of Networking, the non-promiscuous method makes it more difficult for using the analysis and monitoring of the software to diagnose the traffic or the connectivity issues.
The Sniffer can persistently supervise the traffic of a computer via NIC by decoding the encapsulated information on the Data packets.
Kinds of Sniffing
Sniffing is of two types and they are Active and Passive Sniffing
Active Sniffing
In this type of sniffing the traffic is not only monitored but also locked and altered at times to identify the threats. Active sniffing is utilized for sniffing the switch-based network. It incurs injecting the (APR) i.e Address Resolution Packets to the targeted network for flooding the switch (CAM) Content Addressable Memory table. The CAM has the record of all the hosts that are connected to the port. Below are the kinds of Active Sniffing techniques and they are,
- DHCP Attacks
- MAC Flooding
- Spoofing Attacks
- ARP Positioning
- DNS Poisoning
Passive Sniffing
In the Passive sniffing method, the traffic is usually locked however it is not altered at any chance. Passive sniffing only permits you to listen and usually it works on the Hub devices. When you work on the hub device generally all the traffic is sent to the ports. A network that uses a hub for connecting the system, hosts all the networks and you can see the traffic. Hence, the attacker shall easily cease the traffic that is going through. However, in the present days, you need not worry about it as the hubs have turned out to be obsolete. Also, the current modern networks use Switches, and so sniffing is no longer as effective as it was earlier.
Protocols that are troubled
Protocols like the true and tires IP/TCP are devised in a manner that keeps security in mind and hence it does not provide more resistance to the potential intruders. Most of the rules allow themselves for easy sniffing.
- SMTP - It stands for Simple Mail Transfer Protocol and it is applied basically on the transport of emails. It is an efficient protocol however it does consist of any protection that is against sniffing.
- HTTP - It is utilized for sending the information that is with clear text and without any encryption and also this is the real target.
- POP - The abbreviation of POP is Post Office Protocol and this is mainly used for receiving emails from a server. It is the protocol that does not consist of protection against the sniffing as it shall be trapped.
- NNTP - It is also known as the Network News Transfer Protocol that is used for all kinds of communication, however, the major setback of this is that the passwords and even the data are sent via the network as clear text.
- FTP - The File Transfer Protocol is used for receiving or sending the files, however, it does not provide security features. The Data is usually sent as a clear message that shall be sniffed easily.
- Telnet - The Telnet forwards everything like passwords, usernames, and keystrokes through the network as a clear message and so this can be sniffed easily.
- IMAP - It is similar to the functions to that of SMTP, however, this is more vulnerable for sniffing. The IMAP stands for Internet Message Access Protocol.
The Sniffers not only permit you to see the live traffic, when you want to identify all the packets, but you can also do it by saving the capture and thus review it whenever it permits.
Hardware Protocol Analyzers
- The Hardware Protocol Analyzers are the devices that plug into a network on the hardware level and you check the traffic by not manipulating it.
- The Hardware Protocol Analyzers is used for checking and supervising the malicious network traffic that is generated from the hacking software that is installed on the system.
- The Hardware Protocol Analyzer permits the attackers to look at the individual data bytes of all the packets that are passing via cable.
- It can capture the data packet, analyze the content, and decode them based on certain rules.
- These are the hardware devices that are not mostly available for most Ethical Hackers because of huge costs incurred in most cases.
Lawful Interception
It is termed as the Legally sanctioned access for all the communication network data like email messages and telephone calls. The LI should always be in compliance with the lawful authority for the means of evidence or analysis. Hence, LI is the security process on which the service provider or network operator grants the law enforcement officials to access the private communications of the organizations or individuals.
Most of the Countries by now would have drafted and enacted the legislation for regulating the lawful interception procedures. The LI Activities are generally taken for the purpose of cybersecurity and infrastructure protection. Yet the Operators of the Private Network infrastructure shall retain the LI capabilities within its network and it has the inherent right unless it is prohibited.
The LI earlier was known as Wiretapping and it has been in play right from the inception of electronic communications.
Ethical Hacking Course in Bangalore at FITA Academy aids you to have a holistic understanding of the hacking concepts and various hacking techniques under the mentorship of Certified Ethical Hackers.
Ethical Hacking Sniffing Tools
The hackers usually have numerous tools to sniff over the network and also all the tools have their pros. These sniff tools are majorly used for dissecting the information and analyzing the traffic. In this Ethical Hacking Tutorials session, we have enlisted some of the important sniffing tools that are used by the Ethical Hackers.
- Ettercap - It is the complete suite for the man-in-the-middle attacks. It includes content filtering on a fly, live connections, and other intriguing tricks. The Ethercap supports the active and passive operations of various protocols and it consists of the features for the host analysis and network.
- BetterCAP - It is the most flexible, portable, and powerful tool that is developed for performing different kinds of MITM attacks against the network for manipulating the TCP, HTTP, and HTTPS in real-time and much more.
- Wireshark - This is the commonly known and broadly used packet sniffer. This provides a wide number of features that are devised to assist in the operation of the analysis of traffic.
- Tcpdump - This is the popular command-line packet analyzer. It enables the feature to observe and intercept the IP/TCP and the other packets while transmission over a network.
- OmniPeek - It is manufactured by the WildPackets, and the OmniPeek is the commercial product which is the progression of the product EtherPeek.
- Dsniff - The Suite of tools is curated for performing the sniffing with various protocols for the purpose of revealing and intercepting passwords. The Dsniff is devised for the Unix and Linux platform and it does not have a complete equivalent on the Windows platform.
- EtherApe - This is the Unix/Linux tool that is designed for displaying the graphics of the system's incoming and outgoing connections.
- WinDump - It is the Windows port of the famous Linux packet sniffer i.e tcpdump, which is the command-line tool that is the best option to display the header information.
- NetWitness NextGen - This consists of the hardware-based sniffer with features that are devised for analyzing and monitoring the traffic on the network. It is a tool that is utilized by other law enforcement agencies and the FBI.
- MSN Sniffer - This is the Sniffing utility that is primarily devised for sniffing the traffic that is generated by an MSN messenger application.
The Potential hacker can utilize any of these sniffing tools for analyzing the traffic on the network and operating the information.
ARP Poisonning
The Address Resolution Protocol which is also known as the ARP is the stateless protocol that is used for solving the IP addresses to the MAC addresses. Every Network device is required to communicate on network broadcast of the ARP queries in a system to identify the other MAC addresses of the machine. The important thing to note here is that ARP Poisoning is also called ARP Spoofing.
Below are the ways how an ARP function,
- When one of the Machines requires to communicate with the other and it seeks for the ARP table.
- Every Machine on a Network shall compare the IP address to the MAC address.
- When the MAC address is not identified in a table, then the ARP-request is not broadcasted via the network.
- Requesting the computer shall store the address in pairs and its APR table and the communication shall take place.
- When one of the Machines in a network found this address, then it shall reciprocate the APR-request within the MAC and IP address.
ARP Spoofing
The ARP packets could be counterfeited to send the data to an attacker's machine.
A Switch is generally set on the forward mode and then later the ARP table is flooded with spoofed ARP responses, then the attackers shall sniff all the network packets.
The ARP spoofing constructs more number of counterfeited requests and it shall reply to the packets for overloading the switch.
The Attackers flood the target to the computer for ARP cache with counterfeited entries and this is also called poisoning. The ARP poisoning basically utilizes the Man-in-the-Middle access for poisoning a network.
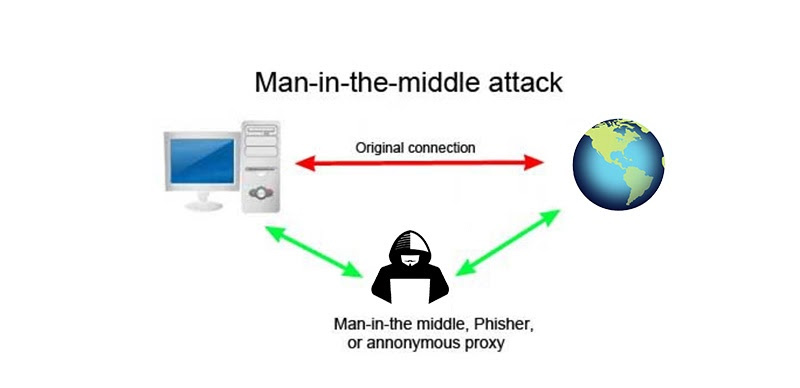
Meaning of MITM
The term MITM stands for " Man-in-the-Middle attack " it is also commonly abbreviated as MIM, MITM, MitM, MITMA, and MiM. This indicates the act of active attacking where an adversary mimics the user on creating the connection between victims and sends messages among them. In that case, the victim shall think they are interacting with each other, however, it is actually the malicious actor who controls the entire communication.
The third person continues to supervise and control the traffic of communication between two different parties. Some of the protocols like SSL serve to forbid the type of attack.
ARP Poisoning - Exercise
In this exercise, you can use the BetterCAP for performing the ARP poisoning the LAN environment using the VMware workstation on which you have installed the Ettercap and Kali tool for sniffing the local traffic on the LAN. To do this, you need the below tools,
- LAN Connection
- Ettercap Tool
- VMware workstation
- Linux or Kali Operating system.
Ethical Hacking Tutorial Notes
This kind of attack is possible only in wireless or wired networks. You shall perform this attack on the Local LAN.
DNS Poisoning
DNS Poisoning is the method that tricks the DNS server to believe that it has earned authentic information while this in reality has not.
The end results will be the substitution of the false IP address and the DNS level where the Web addresses are modified into the Numeric IP addresses. It permits the attacker to replace the IP address entries for the target site on the provided DNS server with an IP address of server controls. The attacker shall build fake DNS entries for a server that may consist of malicious content of a similar name. For Example, a user may type www.google.com, however, the user is forwarded to the other fraud site rather than being directed to Google's servers. As you comprehend, you realize that DNS poisoning is primarily utilized for redirecting the user to the fake pages that are handled by attackers.
DNS Poisoning is more similar to ARP Poisoning. So, in this Ethical hacking basics let us see some of the preventive measures for DNS Poisoning.
Defenses against the DNS Poisoning
- If you are an Ethical Hacker, your work is more likely to place you in a position that shall prevent you from Pen testing. What you should know as the attacker is that it can aid you to prevent the techniques that are employed from outside.
- Here are the defenses that are against the attacks which are covered from the aspect of a Pentester.
- It is advisable to utilize the hardware-switched network for the highly sensitive portions on your network as an attempt to detach the traffic to the collision domain or single segment.
- Deploy the policies to avert promiscuous mode on Network adapters.
- Deploy the IP DHCP Snooping to the Switches for preventing Spoofing attacks and ARP Poisoning.
- Also, be careful while deploying a wireless access point, comprehending that every traffic on a wireless network is susceptible to sniffing easily.
- The Port Security that is used by Switches can be programmed and to permit specific MAC addresses to receive and send data on all ports.
- It is advisable to encrypt the sensitive traffic while using the encryption protocol like IPsec or SSH.
- The IPv6 consists of security options and other benefits that are not available on the IPv4
- The Virtual Private Networks enables the effective defense against the sniffing owing to the encryption feature.
- Restoring the protocols like Telnet and FTP with SSH is an efficient defense in contrast to sniffing. When you find that SSH is not a viable solution, then take into consideration protecting your legacy protocols that are older along with the IPsec.
- The SSL is the best defense with the IPsec.
Scanning Techniques
Scanning is the vital step that is required and it indicates the package of procedures and techniques that are used for finding the ports, hosts, and other services that are available within the network. Network Scanning is an important component of intelligence that helps in collecting and retrieving the information mechanism of an attacker that is used for creating the outline of the targeted organization and it indicates the organization or the group of people who fall as prey to the Hackers. The Vulnerability Scanning is primarily performed by the pen-testers to determine the feasibility of potential network security attacks. And this method paves the way for hackers to detect vulnerabilities like authentication that are weak, unnecessary services, missing patches, or algorithms that are encrypted weakly. So, the Ethical Hacker and the Pen-tester must list down all the vulnerabilities that are identified on the network of an organization.
In this hacking tutorial module, we will dive you deep into the Ethical hacking tricks and tips that are used for Scanning. Let us now see the three kinds of scanning,
- Port Scanning
- Vulnerability Scanning
- Network Scanning
Need for Network Scanning
- For exploring the services that run on the host computer
- For exploring the live computer/host, open ports, and IP address of the victim.
- For exploring the System Architecture and Operating System of a target.
- For dealing with and discovering the vulnerabilities on the Live hosts.
Various methodologies used for scanning
- Usually, the Pen-tester and Hackers seek the Live systems.
- The hacker seeks the open ports.
- Scanning the vulnerability
- Scanning beyond the IDS
- Preparing proxies
Banner Grabbing
It is the kind of obtaining information concerning a targeted system in service or network that are running on their open ports. The tools that are used for performing the Banner grabbing attack are ID Serve and Telent. These pieces of information shall be used by the hackers/ intruders for portraying the set of applicable exploits.
Port Scanning
It is the typical technique that is adopted by predominant Penetration hackers and testers for detecting the open services and ports that are found on the network host. While Port scanning, the hackers must find out the firewalls installed, operating system used, live hosts, and other devices that are connected to the system of the targeted victim/ organization. Upon scanning the victim's system, the hacker fetches the information such as UDP ports, TCP ports, and IP address with this the hacker shall blueprint the victim's network completely under their control. The tool that is used for performing the port scanning is the Amap tool. Generically, the hackers use port scanning as it can easily find the services that could be broken.
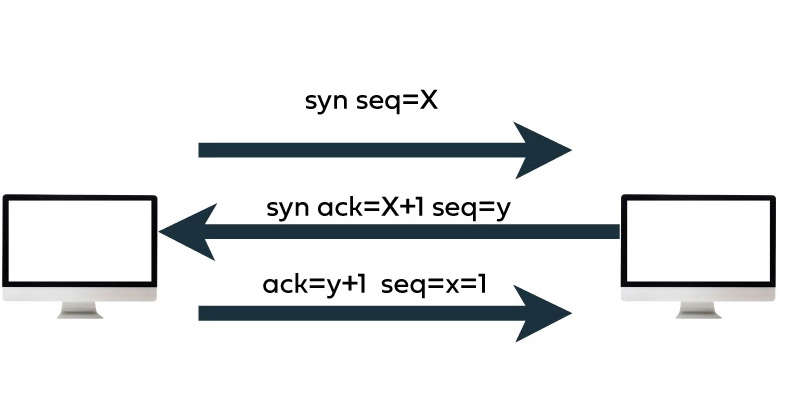
IP/TCP handshake
Before stepping in deep into the scanning techniques, let us have a solid understanding of the 3-way IP/TCP handshaking method. Generally, handshaking indicates the automated process that is used for framing the dynamic parameters of the communication bridge between the two entities that use similar protocols. Over here, the IP and TCP are two protocols that are utilized for handshaking among the server and client. It is the first client that forwards the synchronization packet to establish the connection. Also, the server responds and listens with the syn/ack of the packet to the client. A Client shall respond immediately to a server by forwarding the ack packet. Over here the SYN indicates the synchronization, that is used for booting the connection among the server and client in the packets. The ACK indicates the acknowledgment that is used for showcasing the connection among two hosts.
The different types of scanning techniques are
- XMASScan - It forwards the scanned packet that consists of PSH(push), FIN(finish), and URG (urgent) flags. When you have an open port, then there wouldn't be any response, however, the target shall reply with the ACK/RST packet when the ports are closed.
- SYNScan - The stealth or the SYN scan may not accomplish the TCP three-ways of handshake technique. The Hacker forwards the SYN packet to the victim and when an SYN/ACK frame is earned, then the target shall accomplish the connection and place the port in a position that it can listen. When the RST is restored from a target, then it is presumed that a port is either closed or activated. The SYN Stealth scan is more beneficial as some of the IDS systems log it as the connection or an attack attempt.
- FINScan - The FIN scan replicates more of the XMAS scan excluding the part that forwards the packets just with a FIN(finish) flag and PSH flags or URG. The FIN scan shall accept the same feedback and it has certain limitations as that of the XMAS scans.
- Inverse TCP Flag Scan - The Attackers here forward the TCP probe packets with the TCP flag ( URG, PSH, FIN) or no other flags. When there is no response it denotes that a port is open and the RST is closed.
- IDLEScan - The IDLE scan utilizes the hoax/ spoofed for sending the SYN packet to a specific target on finding the port scan response and the IP header sequence number. Based on the feedback of the scan, a port is detected whether they are opened or closed.
- ACK Flag Probe Scan - The hacker forwards the TCP probe packets to the place where an ACK flag is headed for interpreting header information or the remote device. An RST packet simplifies whether a port is opened or closed. It is fundamentally used for determining the target's filtering system.
- Vulnerability Scanning - This is the proactive assimilation of a system's vulnerability that is within the boundary of the network and this is the automated method that is used for finding whether a system could be threatened or exploited. To execute it successfully, the respective computer should be connected to the internet.
Steps and Tools used
When a Hacker is pushed to execute an ICMP scanning, it is advisable to do it manually. Following are the steps
- Open the Windows O
- Press the Win+R buttons in the mix
- Then, Run the type-cmd
- Then enter the command: ping IP Address or type: ping domain name.
Ethical Hacking Tools that are utilized for scanning the ports and networks
- Angry IP Scanner - It scans the systems that are found on the input range that is provided.
- Nmap - It extracts the details like operating systems, kinds of packet firewalls/ packets, OS version, and the live host of a network service.
- Superscan - It is the other powerful tool that is developed by the Mcafee, that is a TCP port scanner and it is used for pinging.
- ZenMap - This is yet another robust Graphical User interface tool that determines the types of the OS version, OS, port scanning, and ping sweep.
- Hping2/Hping3 - These are the command-line packets that are used for crafting the network for scanning the tools which are utilized for the IP/TCP protocols.
- Omnipeak and Wireshark - These are the popular tools that listen to network traffic and it acts as the network analyzer.
- Net Scan Tool Suite Pack - It is the compilation of various kinds of tools that shall be performed on the flooding, web rippers, portscan, and mass mailers.
Numerous other scanners are found free and they are inbuilt on the Kali Linux OS.
Software and Tools that are utilized by the Mobile scanners consist of a name like Fing, Umit Network Scanner, IP network scanner, Panm IP, PortDroid network analysis, Shadow Sec Scanner, and Nessus Vulnerability scanner.
The names of the other popular PCs are the MegaPing, Advanced Port Scanner, Net Tools, CurrPorts, SoftPerfect Network Scanner, PRTG Network Monitor, and Network Inventory Explorer.
Measures against the Scanning
- Use the custom rules for holding a network or blocking the unnecessary ports.
- It is better to install and configure the IDS and the firewalls properly for identifying and blocking the exact probes.
- The Security Expert must make sure that the proper installation of the anti-spoofing and anti-scanner rules.
- You are required to run the port scanning tools to know whether a firewall has precisely determined port scanning operations.
- The Security experts of the organization should make sure that the Routers, IDS, and also the firewall firmware is updated to the recent release.
Exploitation
Exploitation is a part of programmed software or a script that shall permit the hackers to take the control of a system and thus exploit their vulnerabilities. The Hackers make use of the vulnerability scanners like Nexpose, OpenVas, and Nessus for finding the vulnerabilities.
And Metasploit is termed to be one of the best tools for locating the vulnerabilities on the system.
The exploits are found using these kinds of vulnerabilities. Over here, we shall discuss the best vulnerability of the search engines you can use.
Exploit Database
This is the place where you can identify all types of exploits that are associated with vulnerability. https://www.exploit-db.com/
Common Vulnerabilities and Exposures
The general exposures and vulnerabilities are the standard information and security vulnerabilities names. The CVE is the dictionary of the commonly known information of security exposures and vulnerabilities. This is free for the public use https://cve.mitre.org
National Vulnerability Database
A National Vulnerability Database is a U.S government storehouse of standards-based vulnerability data management. This-data permits the automation of security management, vulnerability management, and compliance. You shall find these databases at the− https://nvd.nist.gov. The NVD consists of the Databases of misconfigurations, product names, impact metrics, software flaws, and security checklists.
Generally, you will notice there are two kinds of exploits
- Remote Exploits - The Local Exploits are usually used by the system that the user has access to the remote network or system. The hackers use remote exploits for obtaining access to a system located in the remote area. is
- Local Exploits - The Local Exploits is usually used by the system that has access to the local system, but doesn't need to overpass the rights.
Ethical hacking tips and tricks
Generally, Vulnerabilities arise because of missing updates. Preferably it is better that you update the systems on a routine.
In the Windows environment, it is possible to activate the automatic updates using the options that are found on the Control Panel -> System->Windows Update.
In the Linux Centos, you can make use of the below command for installing the automatic package update.
yum -y install yum-cron
Enumeration
It belongs to the initial phase of Ethical hacking. It is the process where the attacker develops an active connection with victims and try to find out the attack vectors as possible as they can. In this hacking tutorial, we have explained broadly the concepts of Enumeration.
Usually, the enumeration is utilized for obtaining the details such as
- Network shares
- Usernames of different systems
- SNMP data, if they are not secured properly
- IP tables
The Enumeration rely on the services that are provided by the system such as
- DNS enumeration
- NTP enumeration
- SMB enumeration
- SNMP enumeration
- Linux/Windows enumeration
yum -y install yum-cron
NTP Suite
The NTP Suites are primarily used for the NTP enumeration. It is a prime aspect of the Network Environment. You can identify the other primary servers that aid the hosts to update the time and you shall perform it without authorizing the systems.
Social Engineering
The term Social Engineering is used for a wide range of malicious activities that are accomplished via human interactions. It applies the psychological manipulation tricks with which the users are into making the security or allowing the sensitive information. The Social Engineering attacks usually take place in one or a few steps.
The perpetrator initially identifies the victim for collecting the required background information like weak security protocols, potential points of entry that are required for proceeding with an attack. Later, an attacker shall move the gain of the victim's trust and give the stimuli for frequent actions that shall break the security practices like publishing the sensitive details like providing the access to sensitive resources.
One of the major threats of Social Engineering is that it majorly depends on human error, apart from the vulnerabilities on the software or the operating systems. The mistakes that are committed by legitimate users is much less expected rather than making it difficult to find the thwart other than the malware-based intrusion.
Various Social Engineering Attack techniques
Social Engineering attacks come in various methods and this can function anywhere whenever a human interaction is involved. Below are the general forms of digital social engineering violation.
- Scareware
- Baiting
- Phishing
- Pretexting
- Spear Phishing
Scareware
The Scareware includes the victims that are being battered with fictitious threats. The Users are deceived to think that their systems are affected by malware and thus make them believe that the software installed has no real effect or delude them that the software itself is the malware. The Scareware is also termed as the rogue scanner, deception software, and fraud ware.
The general scareware highlights the legitimate-looking popup banners that appear on your browser at the time of surfing the web, and this exhibits the text. This either allows you to install a tool for you, or this will guide you to the malicious site where the computers are infected. The Scareware is scattered through spam email that shall lend out the bogus warnings and it enables the offers for the users to purchase the harmful or useless services.
Baiting
The very name indicates that a baiting attack uses the false promise for blowing up the victim's curiosity or greed. It lures the users for trapping and then they steal the personal details or inflicting its system with the malware.
The most recalled form of baiting makes use of the Physical media for partitioning the malware. For instance, the attackers leave the bait i.e the flash drives that are infected with malware in noticeable places such as elevators, parking lots, or the targeted company. The bait has the authentic look like a label presenting as a company's payroll lists. Usually, the victims pick this bait out of curiosity and infix them to the work or home computer, or resulting in the robotic malware installation of the system.
The Baiting scams generally need not have to be executed in the physical world. The Online forms of baiting comprise entrapping ads that pave the way to the malicious sites or shall boot the users for downloading the malware-affected application.
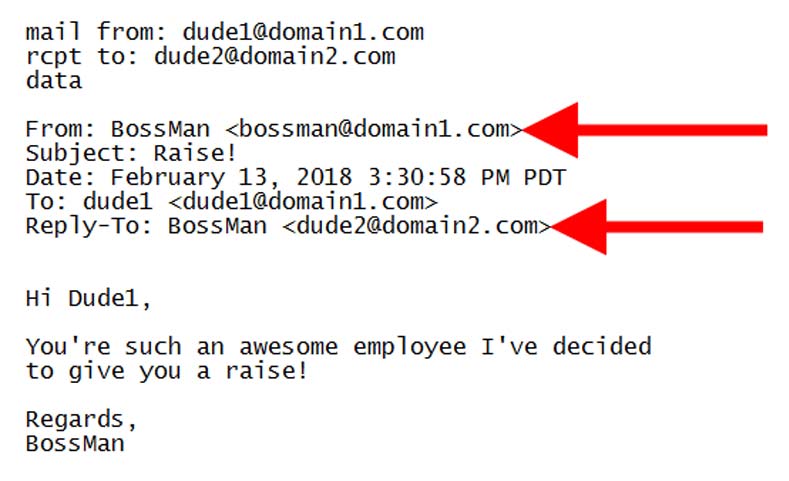
Phishing
Phishing is one of the popular social engineering attacks. Phishing scams are the text and emails campaign that is aimed for creating the sense of curiosity, fear, urgency in victims. It digs them to expose sensitive information, like clicking on the links to the malicious websites or opening the attachments that consist of malware.
An example is a mail that is forwarded to the users of the online service that alerts them with the policy violation that needs immediate action that is part of the required password change. It includes the link of all the illegitimate websitesthat practically identify the appearance of the correct version and then prompts the user for entering the present password and credentials. Right from the submittal of the details are forwarded to the respective attacker.
Provided are the identical or non-identical, messages that are forwarded to all users on the phishing campaigns to block and find them simply from the mail server and granting access to the threat sharing platforms.
Pretexting
Over here, the attackers gain the information via a series of neatly crafted lies. The scam is often prepared by the perpetrator who is seeking the sensitive details of the victims for executing the critical tasks.
Generally, the attackers begin by building trust or hope in their victim by impressing themselves as the bank officials, co-workers, or tax officials who have the rights of authority. The hackers ask the questions that are evidently needed for assuring that the victim's identity via which they shall collect essential personal details. All kinds of suitable records and details are collected using a scam like personal addresses, security numbers, phone records, phone numbers, bank records, staff vacation dates, and other security details that are related to the physical plant.
Spear Phishing
This is more of the targeted version of a phishing scam. Here the attacker chooses the particular individual or the enterprise. Later, they curate the messages to the job positions, characters, and the contacts that accord to the victim for making their attack less noticeable. Spear Phishing needs more time and effort on behalf of a perpetrator and it shall take months time to pull down. It is much more difficult for finding and obtaining better success rates once if it is done skillfully.
The Spear Phishing scenario may involve the attacker who is acting as the organization's IT consultant, and sends the mail to more than one employee. This is signed or worded similarly to a consultant who usually does it and thus entraps the recipients to think this is the authentic message. Usually, the message prompts the recipient for changing their password and provides them with the link that shall redirect them to the malicious page where the attacker shall capture the credentials.
Trojans
The Trojans are the Non-replication programs that may not produce their codes by affixing themselves with the other executable codes. It shall operate without any knowledge or permission of computer users.
The Trojan shall shelter themselves in a safer manner. Yet, you can note that the Trojans shall affect it outside the machines only with the guidance of the computer user such as choosing the file that shall be attached with the mail from the unknown person, opening unsafe URLs, and plugging the USB without any scanning.
The Trojans have numerous malicious functions. In this Ethical Hacking tutorial, we have jotted down Trojan and its concept in detail.
It can build the backdoors to the system. The Hackers shall make use of all these backdoors for accessing the victim's files and system. The Hackers shall use the Trojans for deleting and editing files that should be present on the victim's system or to supervise the activities of a victim.
- A Trojan can utilize the victim's computer for attacking the other system of Access and Denial services.
- A Trojan shall steal all the financial data such as transaction details and bank account details. It is called the Trojan-Banker.
- A Trojan shall encrypt all the files and the hacker shall henceforth demand money that is required for decrypting it. It is called Ransomware Trojans.
- They can also use the phones for sending the SMS to third parties. It is called the SMS Trojans.
Trojan Information
When you have found out about the virus and when you need to instigate further with regards to its function then it is suggested you shall look at the below virus databases that are offered usually by the antivirus vendors.
- F-secure - https://www.f-secure.com
- Symantec - Virus Encyclopedia - https://www.symantec.com
- Kaspersky Virus Database - https://www.kaspersky.com
Ethical Hacking Tips and Tricks
- Install the best antivirus and it should be kept updated.
- You should not open the email attachments that are coming from the unidentified resources.
- You need not accept an invitation that is from unknown people from social media.
- You need not open the URLs that are forwarded by the unknown URLs or people in a weird method.nbsp;
Ethical Hacking Course in Coimbatore at FITA Academy upgrades your hacking skill sets with recent practices that are followed in the industry under the guidance of Experts Ethical Hackers with certification.
TCP/IP Hijacking
The IP/TCP Hijacking occurs when the authorized user obtains access to the legitimate network connection of the other user. This is done to detour the password authentication that is usually the beginning of the session.
On the theoretical aspect, the TCP/IP connection is vested as depicted below:
For hijacking the connections there are two ways
- First, find the seq on which the number is increased by 1, however, there is less chance to anticipate it.
- The next possibility is that you can apply the Man-in- Middle attack, in a nutshell, it is called network sniffing. To perform the sniffing you can use the tools such as Ethercap and Wireshark.
For instance,
The attacker shall supervise the data transmission over the network and find the IP's of the two devices that take place on the connection. When the hacker finds that the IP of any of the users, then the hacker can place lower the connection of the rest of the user by applying the DoS attack and later presume the communication by cutting the IP of a disconnected user.
Shijack
The best tool for the TCP/IP hijack is the Shijack tool. It was built using the Python Language and you shall download them from the link that is given below https://packetstormsecurity.com/sniffers/shijack.tgz
Below is the example of Shijack command −
root:/home/root/hijack# ./shijack eth0 192.168.0.100 53517 192.168.0.200 23
Over here we are trying to hijack the Telnet connection among two hosts,
Hunt
The Hunt is also the other popular tool that you shall use for hijacking the IP/TCP connection. You can download it from https://packetstormsecurity.com/sniffers/hunt/
Ethical Hacking Tips and Tricks
All the sessions which are not encrypted are susceptible to IP/TCP session hijacking and so you must be the one who uses the encrypted protocols sooner. Or else you must be able to make use of the double authentication technique that shall try to keep the session secured.
Physical Security
A prominent number of people think that hacking shall take place from the point of logical security alone. However, Physical security is the fact that concerns both the penetration tester and the malicious hackers. The Penetration testing adjacent to the Physical target is also a general phase of testing. In this Hacking Tutorial, we have listed down what Physical Security is all about and also the objectives of Physical Security.
Physical Security shall be explained as the concern that is associated with hard drives, organization's machines, computers, laptops, servers, and details that are related to the asset storage devices. These are the kinds of protection that should be given more importance as the real-world threats are maximum of natural disaster or unauthorized access. It is the kind of security that needs Physical controls like protective barriers, locks, uninterrupted power supply, security personnel to safeguard the private and confidential data that are stacked on the servers, and also the in-penetrable doors or walls.
Physical Security vs Information Security
These two terms have a significant conceptual difference. Firstly, let us comprehend what are they
- Information Security is concerned with the protection of information from unauthorized access such as modification of information, disclosure, recording, illegal use, destroying information, or copying.
- Generally, Information Security is subjected to a Logical domain while Physical security is subjected to the Physical domain.
The Objectives of the Physical Security
- Comprehend the requirement for the Physical Security
- Analyze the threats to information security that are associated with Physical security.
- Defines the main physical security consideration to choose the facility site.
- Find out the Physical Security to monitor the components.
- Demonstrate the component of the response and fire detection.
- Know the significance of the fire safety programs.
Different factors that determine the Physical Security Vulnerabilities
Any kind of hacking type at a specific time may result in success, however, the security shall be affected adversely when the hacker obtains access to an organization's building or the data center. In any small scale organization or company, the chances of Physical Security Vulnerability shall be comparatively less. However, the other factors, upon which the Physical Security Vulnerabilities rely on are as follow:
- The Number of Employees who works in an organization
- The Size of a building
- The Number of Entry and Exit Points that are there in the building
- Location of the Data Centers and the other Confidential details
- The Number of Buildings, Sites, and Workplaces that are there in the organization.
Different Layers of Physical Security
Physical Security relies on the layer of defense model similar to that of the information security. These Layers are infused at the perimeter and it is moving toward the asset. The layers include,
- Deterring
- Delaying
- Assessment
- Delaying
- Response
- Detection
Weak Points that shall Compromise the Physical Security
The Hackers usually assume themselves as the mastermind and look for the maximum exploits on the buildings for the Physical unauthorized access. Right from the view of an attacker, below are the places or situations where the Physical Security is compromised.
- Looking for the gap beneath the critical doors which permits someone to use the device for tripping the sensor that is present inside the security room.
- Finding the possibilities whether it would be easy to open a door either by opening the door or by breaking the door forcefully.
- When the doors are propped open and, when it is so like that, it shall be the attack vector.
- The possibilities of door ceilings with the tiles could be pushed up.
- Looking for the Windows and Doors that are made up of glass. Specifically looking for the Server door or room and the other confidential locations that are made up of glass.
- Identifying whether the Power supply and Protection of equipment is completely faulty.
- Gaining Network Access later the hackers send threatening emails as though they are logged-in users.
CPTED - Crime Prevention Through Environmental Design
It is the practice that blueprints how a proper layout of the real scenario shall mitigate hacking and crime by affecting human behavior directly. It is the notion that was developed in the time of the 1960s and this is still applied especially for preventing social engineering. It consists of three main strategies and they are
- Natural Surveillance
- Territorial reinforcement
- Natural Access Control
Assessment of Risk
The Cybercriminals, as well as the Physical intruders, function on the same motto that is to threaten and obtain money or fulfill any of their social agenda. These intruders seek opportunities for exploiting the security by any means or method. And so Motive, Means, and Opportunity are the three main purposes for a hacker to threaten an individual or an organization.
Protection and Countermeasures Techniques
Physical Security consists of the fact that the security controls are commonly reactive. Other than the Experts it is required to be included at the time of idea assessment and it modifies the stages from the perspective of security. Apart from this, the Security, measures should be given special care and they are,
- Fences
- Walls with a window near data centers
- Strong Locks and Doors
- Security Cameras and Lights are around the entry and exit points.
- The Intrusion detection system should be applied for determining the illegitimate entries and it is required to alert the possible entry.
- The IP-based network or the CCTVs, Closed-Circuit Television cameras are required for monitoring and using them in real-time.
- The Security guards and the personnel should be used for protecting the data against physical damage or theft.
- Learn the various types of IDS systems like the Volumetric and Electromechanical
- An organization should use the basic service of the Biometric access system.
- The different kinds of lock system should be applied like programmable locks, biometric locks, manual locks, electronic locks, and automatic locks.
- The tiers of the Physical security within the information access control like the Name badge and ID card.
- The Alarm System must be installed on the building infrastructure for prompting in the case when an event occurs, the events include theft, fire detection, environmental disturbances, intrusion detection, and interruption in the services. Ethical Hacking Course in Pune at FITA Academy is a complete hands-on training program that equips the learner's knowledge and skillsets on the Ethical hacking concepts under the guidance of real-time Ethical Hacking professionals with certification.
Email Hijacking
Email Hacking is the global menace at present. Email Hijacking is functioned using the three techniques and they are inserting viruses, social engineering tools, and email spoofing in the user computer.
Email Spoofing
In email spoofing, a spammer forwards the email from the known domain to make the receiver believe that they knew this person and so they open the mail. These emails usually consist of doubtful content, suspicious links, and the need to transfer the money.
Social Engineering
The Spammer forwards the promotional emails to different users to provide more discounts and thus entrap them to fill in their data. You have the tools that are found in the Kali which head you to hijack the email.
Email Hacking can also be executed using Phishing techniques. The below image is an example of Email Hacking.
All the links in an email shall install the malware into the user's system and redirect them to a malicious website and shall trick them to reveal financial details and personal information like credit/debit card details, passwords, and account IDs
A Phishing attack is generally used by most cybercriminals, as it is way easier to trick someone to click on the malicious links in an email rather than trying to break via the computer's defenses.
Implant the Viruses in the User System
This is the third method through which the hackers shall hijack your email account. And it is executed by infecting your system with a virus or other type of malware. By implanting the virus into your system the hacker shall obtain all your credentials and passwords.
How can you determine whether the email has been hijacked?
- When you strive to access the account and password but it does not work anymore.
- A recipient of the spam emails consists of the set of people you will know.
- When your sent items folder consists of a set of spams that you yourself shall not be aware of forwarding.
- When you are intended to access the " Forward Password" link and when you don't get the email that you expect.
- When your Sent Item folders consist of a set of spams that you are not aware of.
Ethical Hacking Tips and Tricks
In this stance, you shall think that your email is been hijacked, then you must take of the below actions,
- It is advisable to change your passwords immediately.
- Install the best antivirus on your system/computer and update them.
- Caution your friends not to open the links that they get from your email account.
- Have a double authentication password when the application enables that feature.
- Reach your immediate authorities and inform them that your account has been hacked.
Password Hacking
When you have the passwords for the databases, emails, bank accounts, computer systems, servers, and virtually all that are required to be protected. The Passwords are usually the keys that are utilized for accessing the account or system.
Generally, people keep passwords that are easy to remember like mobile numbers, dob, or the names of their closed ones. It is what makes the passwords weaker and they are prone to hacking easily. One must always look after that they should have a strong password that helps in defending their account from the essential hackers. The Strong password have the attributes of the following,
- Consists of 8 Characters
- The mix of numbers, special characters, and letters
- The combination of capital and small letters.
Dictionary Attack
In this method, the hacker uses the predefined set of words from the dictionary for guessing the passwords. When the set of passwords are weak, it is easy for the dictionary attack to decode them quite fastly.
Hydra is the most popular tool which is utilized for a variety of dictionary attacks. Have a look at the below screenshots and you will observe how you can make use of the Hydra for identifying the password of the FTP service.
Hybrid Dictionary Attack
The Hybrid dictionary attack makes use of the group of dictionary words that are combined with extensions. For instance, when the word "admin" joins itself with a number of extensions like "admin125" and " admin147", etc.
The Crunch is the Wordlist generator where you can mention the specific standard or the character set. The Crunch shall generate all kinds of permutation and combinations. This tool comes with the bundle of the kali distribution of Linux.
Brute - Force Attack
When the Brute-force attack takes place, the hacker shall make use of all the possible sequences of special characters, numbers, numbers, small & capital letters for breaking the passwords. It is the kind of attack that has the highest probability of success, however, it needs more time for processing all types of sequences. The Brute-force attack is the slowest and the hacker shall not need the system with a robust processing power to execute all types of permutation and combinations faster.
“Johnny or the John the Ripper” is a robust tool which is the set of brute-force attacks and it shall come in packed with a Kali distribution of the Linux.
Rainbow Tables
The Rainbow table consists of a group of predefined passwords which are usually hashed. This is the lookup table that is used for regaining the lucid passwords from the ciphertext. At the time of password recovery, it is more similar to the pre-calculated hash table that shall crack the password. You can download the tables from http://project-rainbowcrack.com/table.htm
The Rainbow Crack 1.6.1 is a tool that is used in the rainbow tables. This is again found in the Kali distribution.
Ethical Hacking Tips and Tricks
- Set the Strong passwords that are hard to crack
- Use the set of combinations like digits, symbols, capital and small letters, and alphabets
- Just don't note down or make a note of the password and just don't memorize.
- Just don't set passwords that are the same as that of other usernames.
Ethical Hacking - Wireless Hacking
The Wireless Network is the collection of more than two devices that are connected through radio waves within the confined range. The devices on the wireless network have the liberty to be in flux, however, they should be connected to the network and they must share the data with the other devices on the network. The vital aspect over here is that they are widespread to the extent that their cost of installation is much rapid and affordable when compared to the wired networks. Wireless Networks are used widely and it is easier for the setup process. Usually, the Hackers use the IEEE 802.11 standards. Over here, the Wireless router is the most important device on the Wireless network which helps in connecting the user to the Internet.
On the Wireless Network, you have the Access Points that are the Extension of the Wireless ranges which acts as the logical switches.
Though the Wireless Networks provide the best flexible feature, it has concerns with the security issues. The Hacker shall sniff the network packets without being on the same building in the site where your network is located. The Wireless Network shall communicate via radio waves and the hacker shall easily sniff the network from the nearer location. Generally, the attackers shall perform the network sniffing to identify the SSID and then hacks them into the wireless network. If your wireless cards are modified into sniffing models, then it is called the monitor mode.
Here in this Ethical Hacking Tutorial, we are going to see how to crack the wireless network and the tool that is used in this process.
Wired Equivalent Privacy
Wired Equivalent Privacy is also popularly called WEP. It is developed based on the standards for the IEEE 802.11 WLAN Standards. The aim of this is to enable the privacy equivalent to that of the wired networks. The WEP functions by encrypting the data which have been transmitted through a network for protecting it from potential threats.
How to Crack the Wireless Networks
Cracking is the method of exploiting the security weakness in the Wireless network and obtaining unauthorized access. Usually, the term WEP Cracking indicates exploitation that takes place on a network that uses the WEP for deploying the security controls. Cracking is of two types and they are
- Active Cracking - It is the kind of attack that has boosted the load effect on network traffic. This is way easier for determining the network exploitation when compared to passive cracking. This is effective when you compare it to the passive cracking
- Passive Cracking - It is the kind of cracking which has no or zero effect on network traffic till the WEP security is cracked. Also, this is more difficult for determining.
Ethical Hacking Tools
- Aircrack - It is the WEP cracker and network sniffer. You can download it from http://www.aircrack-ng.org/
Kismet
It is the robust tool that is used for wireless sniffing which is identified in the Kali distribution. You can also download it from the official webpage - https://www.kismetwireless.net
As displayed in the picture, just click on the Start button.
Now, the Kismet shall begin to capture the data. The below screenshot shall display how it shall appear.
Net Stumbler
This is the other wireless hacking tool that is primarily used on the Windows system. You can download them from http://www.stumbler.net/
This is simple for using the NetStumbler in your system. You should just click on the scanning button and then wait for the results. For your reference look into the below image.
The important thing here is that your card must support the monitoring mode, or else it shall fail to monitor.
WEP Crack - It is the Open-Source Program that is used for breaking the 802.11 WEP secret keys. This is deployed on the FMS attack http://wepcrack.sourceforge.net/
Web Decrypt: It is the tool that makes use of the active dictionary attacks to crack the WEP keys. The Web Decrypt has its own implements and generator packer filters. You can download it from. http://wepdecrypt.sourceforge.net/
Wireless DOS Attacks
In the Wireless environment, the attacker shall attack the network from a specified distance, and henceforth, it is laborious to gather evidence against an attacker. The first kind of the DoS is the Physical Attack. It is the kind of attack which is fundamental. And this kind of attack is done from the base of the radio interferences that can be developed even from the cordless phones that shall operate on the frequency of 2.4 GHz.
The other kind of attack is Network DoS Attack. The Wireless Access Point develops the shared medium that enables numerous possibilities to flood traffic to this medium and forwards the AP that will make the processing slower than the clients who shall try to connect. These attacks shall be built by using the ping flood DoS attack. The Pyloric is the popular DoS tool from which you can download from https://sourceforge.net/projects/pyloris/ Also, the Low Orbit Ion Cannon is the other popular tool that is primarily used for the DoS attacks.
Ethical Hacking Tips and Tricks
For Securing the Wireless Network, you must have the following points in your mind,
- Modify the default password of the access points
- Modify the network password and SSID regularly
- Turn off the Guest Networking
- Avoid using the WEP Encryption
- Update the firmware of the wireless device.
DDOS Attack
Hackers have numerous reasons behind breaking into network security. Regardless of the purpose behind the hacking, it causes equal damage for both individuals as well as the organization that has become the prey. This can have a tremendous effect on the business firm which can also lead to a loss of more than a million dollars. Though more security services are deployed and advanced security methods are adopted widely across the organization. It is sure that it is impossible to guarantee 100% security.
In this hacking tutorial session, you will learn about the (DDoS) Distributed-Denial of Service functions and the steps that are needed for protecting an individual and as well as the business sites from these computer attacks.
Firstly, let us get acquainted with what a DDoS is.
It is the kind of attack on the network and computer that prohibits, prevents, or reduces the system from retrieving the accessibility to the legitimate users. This is the kind of attack on which the intruder or attacker puts efforts to deprive the authorized or system users of access to their sites, networks, or computers. The thing you should note here is that an attacker primarily aims at the bandwidth of a victim for performing the attack.
The Malicious utilization of resources internally within the organization shall produce the output of the Denial of Service attack. According to the recent statistics, it is stated 95% of “cases where the attacker intended to destroy and not to steal using the Denial of Service”.
Indication of the Denial of Service Attacks
- A DOS usually results in the following,
- Hanging a system
- Slower performance of the network
- Shutting down or Rebooting the specific system
- Idle responses from the system
- Incapable of accessing any websites
- Unable to reach the targeted website
- You can see a radical increase in the Spam emails you receive
- Deleting and Damaging the hardware or network resource
- Mishaps of information from the victim's site or computer
- Crash of the Programs and Data of the users which were found online at the time of the attack
- Detaching Wired or Wireless Internet connection
When the Denial of Service attack is executed adequately for an ample amount of period on the large scale, then the Internet connectivity of the complete geographical region shall be compromised without the knowledge of the attacker and that the attack has occurred. Hence, the Denial of the Service attack includes the system by not intruding which are not sufficient enough for complicating the network infrastructure or the functionality of the organization.
General DoS Attack Types
- Bandwidth Attack - The Single machine shall not withstand more number requests to astound the network equipment and so more packets are pushed at a time for flooding in the victim's network or a large number of the pings to the targeted website.
- Buffer Overflow - It is the general type of Denial of the Service attack that is forwarded to large traffic via the addressed network. The Attacker may identify the vulnerabilities to a target system that shall be exploited, or the attacker shall hardly make the trail to attack in case if it functions.
- Teardrop Attack - This is the kind of Denial of Service attack that shall exploit an Internet Protocol (IP) that depends upon the packet which is too huge for the next router for handling and this can be split into fragments. And now this packet fragment later finds the offset that allows the complete group of packets to be mobilized by the receiver or the computer. In this type of attack, the attacker's IP sets a complex offset value that begins right from the position of the second fragment. In case when the receiving OS doesn't have a caution for this attack vector, then it can result in a severe crash to the system.
- SYN attack - Over here, the attacker, forwards numerous SYN packets to the targeted server of a victim along with the fake IP address.
- Physical Infrastructure DoS - Here, someone shall nick the fiber-optic cable to the current network hardware infrastructure. By using this method, then the traffic via the network shall be routed easily.
- P2P attack - By using the peer-to-peer attack, the attacker shall guide the clients or the peers who are connected to a network to disconnect from its peer-to-peer network and later make them connect to the fake website of the victim. And here, a mugger exploits the network flaws by using the (DC++) Direct Connect protocol that is used for sharing all kinds of files among the Instant Client i.e Instant Messaging.
Knowing What Distributed Denial of Service Attack
The DoS attack is replaced along with the name of Distributed Denial of Service (DDoS) attack when the multitude of the hacked systems focus on the specific system. In a nutshell, whenever the Denial of Service attack is executed using different compromised devices for attacking the specific system, then the distributed nature of an attack is labeled as the Distributed Denial of Service (DDoS) attack.
Typically, in the DDoS attack, the attacker or the mugger begins exploiting the vulnerability in one system or computer and thus makes it the DDoS master which is not but the other vulnerable computer that is determined via the computer and classified. Later these infect the systems along with the malware.
For launching the Distributed Denial of Service attack, in your DDoS master system, the attacker shall utilize the botnets to affect and then administer numerous computers and attacks a single system.
Over here the attack is labeled as "distributed" as a different computer is manipulated by the hackers for performing the DDoS attack.
Measures to avoid the DoS and DDoS kinds of attack
Unluckily, there are no 100% of successful methods to protect the victim from the prey who are intended to perform the DoS/DDoS attacks. However, the users shall make use of few prevention tactics to reduce the possibility of the attacker using the computer for attacking the others. Below are some of the important prevention tactics.
- Download and Configure the Antivirus Software along with the recent updates.
- Download the firewall and configure it to the latest updates for restricting the traffic.
- Apply the filters to the emails for handling the unwanted traffic.
Factors on which the Attackers look for
- The exploitation of the Internal Resources - Here the attackers make the effort to crunch resources for few machines along with the aftermath that the utilization of network bandwidth shall be huge and the wastage with it will be the non-available resource to others.
- The attack against Connectivity - This is a mode of attack, where the attacker develops numerous packets from a system to which the attack is planned. The consumption of bandwidth has significantly reduced to the slowdown of the attack and network.
- Altering Configuration - This is a kind of attack, where the attacker puts effort to fleece the misconfigured details that are available on a network for the DoS.
Ethical Hacking tools that are used for DoS Attack are as follows,
- Bubonic
- UDP Flood
- Targa
- Jolt 2
- Namesy
- Blast 20
- Panther 2
- FS max
- Crazy Pinger
Security and Countermeasures against DDoS
- Degrading Services - Finding and ceasing the noncritical services
- Service Shut Down - By applying this technique, every service shall be shut down till the attack has been subsidized.
- Interrupting the attack- It is the protection technique that needs more preplanning and it needs the additional capacity for withstanding or consuming the attack.
Ethical Hacking Course in Gurgaon at FITA Academy equips the knowledge of the participants with required tools, techniques, and tricks under the mentorship of certified Ethical Hacker with real-time practices.
SQL Injection
It is the group of SQL Commands that are planted in the Data Structure or a URL string for restoring the response you need from the Database which is connected to the Web applications. It is the kind of attack that usually occurs on the Web Pages that are built using the programming language PHP or ASP.NET
The SQL injection attack shall be performed with the below intentions:
- For dumping the complete database of the system
- For performing various queries that are not permitted by the application
- For changing the content of a database
This kind of attack applies when the applications missed validating the inputs accurately, prior to pushing them to the SQL Statement.The Injections are usually placed on the search fields, address bars, and data fields. It is the simplest way for determining the web application that is vulnerable to the SQL injection for attacking and to make use of the " ' " characters in the string to see whether you receive any error.
For instance,
To comprehend this concept we have used it in a few examples.
As shown in the following screenshot, we have utilized the " ‘ " character in the Name field.
You can now click on the Login button. When you do that it will produce the following output.
SQL Map
The SQLMAP is the best software that is available for detecting SQL injections. You can download them from the http://sqlmap.org/
It is by default compiled on the Kali distribution. You can find them from the below-given path - Applications → Database Assessment → Sqlmap.
Once opening the SQLMAP, you can move to the page that consists of the SQL injection. And then it receives the header request. Now you can run the below command in the SQL from the header,
The SQLMAP shall test the variables and then produce the result as the parameter "id" that is vulnerable, you can see them from the below screenshot,
Ethical Hacking Tips and Tricks
For protecting your Web Application from the SQL injection attacks, you must make note of the below points,
- The User input that is passed into a database must be quoted.
- All the variables that pass into an application must be validated and sanitized.
- The Unchecked user-input for the database should not be permitted to pass via the application of the GUI.
Pen Testing
Penetration Testing is the most common method which most companies follow to minimize its security breaches. It is the controlled method of hiring the professional who tries to hack into your system to showcase to you the loopholes that you must fix. Before performing the penetration test, it is important to cohere to the parameters that are mentioned in the agreement and they are
- The time of the Penetration test
- The place where the IP Source of attack shall be
- And what are penetration fields that are found on the system?
Generally, the Penetration testing is executed by professional Ethical hackers who primarily use automated tools, open-source tools, commercial and manual checks. You have no restrictions and the important objective of this is to expose the security flaws that can take place.
Different Types of Penetration Testing
- Grey Box - It is the kind of Penetration testing where an Ethical Hacker possesses halfway knowledge of infrastructure, just like the name of the domain server.
- Black Box - In this type of testing, the Ethical Hacker does not have any details associated with the network or infrastructure of the organization which the hacker is trying to penetrate. In this testing, the hacker usually implies more effort into finding out the details using the name of the hacker himself/herself.
- White Box - In the White-Box penetration testing, the Ethical Hacker is given all the basic details of the network and infrastructure of the organization that is needed for penetrating.
- Internal Penetration Testing - In this kind of testing the Ethical hackers are found inside the network of a company and the hacker conducts the test from here.
- External Penetration Testing - It is the type of testing that primarily focuses on the Server or the network infrastructure and the operations of the software under its infrastructure. Here, the Ethical Hacker tries to attack the public using the networks via the Internet. The hacker tries to hack the infrastructure of the company by attacking the web servers, DNS servers, and web pages.
The Penetration testing shall cause the problem of system crashes, data loss, or system malfunctioning. Hence, the company must calculate the risks before moving ahead with the penetration testing. The risk is calculated using the below formula and the management risk.
Risk = Threat * Vulnerability
Ethical Hacking Tips and Tricks
Before moving to the Penetration test, you must have the below points in your mind,
- First and foremost try to comprehend all your requirements and evaluate every risk.
- Recruit a Certified person for conducting the Penetration test as they are trained for applying all the feasible techniques and methods for unveiling the possible loopholes to the network or the web application.
- Also, always sign in to the agreement before performing the penetration test.
Ethical Hacking Skills
When you want to qualify yourself as Ethical Hacker, you must initially learn about different hacking techniques like
- Network traffic sniffing
- Session spoofing
- Session hijacking
- Password cracking and guessing
- Denial of Service Attacks
- SQL injection
- The exploitation of the buffer overflow vulnerabilities
In this Hacking tutorial session, we will guide you through the important skills that are needed for becoming an expert in the Ethical Hacking
Computer Hacking is both Art and Science as well. Like the other expertise, you should put in more effort for obtaining knowledge and to become an expert hacker. Once you step into the work-life environment you need more effort to constantly be updated on recent technologies, exploitation techniques, and new vulnerabilities.
The Ethical Hacker should be a Computer System Expert and they should also have a demonstrable understanding of computer networking and programming skills.
The Ethical Hacker must have the attribute of perseverance, patience, and persistence for trying again and again and thus wait for the desired result.
Furthermore, the Ethical Hacker must be sharp and intelligent enough to comprehend the situation and the other user's minds that are set to use the social engineering exploits to threaten your system. Generally, a good Ethical Hacker must possess good problem-solving skills.
Certification and Courses
If you are planning to set your career or uplift your career in the domain of Cyber Security and Ethical Hacking domain you shall pursue any of the certification courses.
- Obtaining a degree certificate from the branch of Computer Science or Software technologies.
- Having the additional network certifications such as CCNA or Networking and Security certification like CISSP or the TICSA.
- Going through Ethical Hacking Tutorial to become efficient with various security aspects of Computers and Networks.
- Read the Study Courses that include the topic such as backdoor viruses, viruses, trojan horses, denial of service attacks, buffer overflow, SQL injection, system hacking, social engineering, footprinting, reconnaissance, penetration testing, and session hijacking.
Last, but not least, you can step into an organization for learning the Ethical Hacking notions proficiently from the basics. Where they train you in a manner to take-up the Certified Ethical Hacking Certification exam.
Apart from the CEH Certification obtaining Offensive Security Certified Professionals (OSCP) and Global Information Assurance Certification (GIAC) are the additional IT security certificates that help you to add on to boost your profile value.
Endnotes
With the advent of technologies and rapidly booming data, Ethical Hacking is one of the mainstream careers at present with enormous opportunities for career growth. Anybody who opts for this domain shall have a futuristic career. As the organization's in the upcoming days seek more and more Ethical hacking professionals who can protect the security and compliance of the respective organization. Ethical Hacking Course in Chennai at FITA Academy provides you both Online and Offline modes of classes in different cities across India. You can enroll in the Ethical Course @ FITA Academy where you will be provided with complete guidance and training to head-start your career. Hope this Ethical Hacking tutorialv helped you with all your learning needs!
Interview Questions
Interview Questions on Digital Marketing Java Interview Questions For Experienced Selenium Interview Questions and Answers For Experienced Hadoop Interview Questions and Answers For Experienced Python Interview Questions and Answers For AWS Interview Questions and Answers For Experienced DevOps Interview Questions and Answers Oracle Interview Questions PHP Interview Questions For Freshers AngularJs Interview Questions RPA Interview Questions Software Testing Interview Question and Answer Mobile Testing Interview Questions and Answers Salesforce Interview Questions Networking Interview Questions and Answers Pega Interview Questions NodeJS Interview Questions Ethical Hacking Interview Questions Data Science Interview Questions and Answers Javascript Interview Questions Blue Prism Interview Questions SEO Interview Questions Android Interview Questions MS Excel Interview Questions Cloud Computing Interview Questions Cyber Security Interview Questions Interview Question on Tableau Power BI Interview Questions and Answers Artificial Intelligence Interview Questions and Answers Azure Interview Questions and Answers SQL Interview Questions and Answers Full Stack Interview Questions and Answers Dot Net Interview QuestionsFull Stack Interview Questions and Answers UI UX Interview Questions and Answers ReactJs Interview Questions Full Stack Interview Questions and Answers Linux Interview Questions
Contact Us
For Business
Testimonials
Resources
Follow Us
TRENDING COURSES
JAVA Training In Chennai Core Java Training in Chennai Software Testing Training In Chennai Selenium Training In Chennai Python Training in Chennai Data Science Course In Chennai C / C++ Training In Chennai PHP Training In Chennai AngularJS Training in Chennai Dot Net Training In Chennai DevOps Training In Chennai German Classes In Chennai Spring Training in ChennaiStruts Training in Chennai Web Designing Course In Chennai Android Training In Chennai AWS Training in Chennai
iOS Training In Chennai SEO Training In Chennai Oracle Training In Chennai RPA Training In Chennai Cloud Computing Training In Chennai Big Data Hadoop Training In Chennai Digital Marketing Course In Chennai UNIX Training In Chennai Placement Training In Chennai Artificial Intelligence Course in ChennaiJavascript Training in ChennaiHibernate Training in ChennaiHTML5 Training in ChennaiPhotoshop Classes in ChennaiMobile Testing Training in ChennaiQTP Training in ChennaiLoadRunner Training in ChennaiDrupal Training in ChennaiManual Testing Training in ChennaiWordPress Training in ChennaiSAS Training in ChennaiClinical SAS Training in ChennaiBlue Prism Training in ChennaiMachine Learning course in ChennaiMicrosoft Azure Training in ChennaiSelenium with Python Training in ChennaiUiPath Training in ChennaiMicrosoft Dynamics CRM Training in ChennaiUI UX Design course in ChennaiSalesforce Training in ChennaiVMware Training in ChennaiR Training in ChennaiAutomation Anywhere Training in ChennaiTally course in ChennaiReactJS Training in ChennaiCCNA course in ChennaiEthical Hacking course in ChennaiGST Training in ChennaiIELTS Coaching in ChennaiSpoken English Classes in ChennaiSpanish Classes in ChennaiJapanese Classes in ChennaiTOEFL Coaching in ChennaiFrench Classes in ChennaiInformatica Training in ChennaiInformatica MDM Training in ChennaiData Analytics Courses in ChennaiFull Stack Developer Course in ChennaiHadoop Admin Training in ChennaiBlockchain Training in ChennaiIonic Training in ChennaiIoT Training in ChennaiXamarin Training In ChennaiNode JS Training In ChennaiContent Writing Course in ChennaiAdvanced Excel Training In ChennaiCorporate Training in ChennaiEmbedded Training In ChennaiLinux Training In ChennaiOracle DBA Training In ChennaiPEGA Training In ChennaiPrimavera Training In ChennaiTableau Training In ChennaiSpark Training In ChennaiGraphic Design Courses in ChennaiAppium Training In ChennaiSoft Skills Training In ChennaiJMeter Training In ChennaiPower BI Training In ChennaiSocial Media Marketing Courses In ChennaiTalend Training in ChennaiHR Courses in ChennaiGoogle Cloud Training in ChennaiSQL Training In Chennai CCNP Training in Chennai PMP Training in Chennai OET Coaching Centre in Chennai
Are You Located in Any of these Areas
Adambakkam, Adyar, Akkarai, Alandur, Alapakkam, Alwarpet, Alwarthirunagar, Ambattur, Ambattur Industrial Estate, Aminjikarai, Anakaputhur, Anna Nagar, Anna Salai, Arumbakkam, Ashok Nagar, Avadi, Ayanavaram, Besant Nagar, Bharathi Nagar, Camp Road, Cenotaph Road, Central, Chetpet, Chintadripet, Chitlapakkam, Chengalpattu, Choolaimedu, Chromepet, CIT Nagar, ECR, Eechankaranai, Egattur, Egmore, Ekkatuthangal, Gerugambakkam, Gopalapuram, Guduvanchery, Guindy, Injambakkam, Irumbuliyur, Iyyappanthangal, Jafferkhanpet, Jalladianpet, Kanathur, Kanchipuram, Kandhanchavadi, Kandigai, Karapakkam, Kasturbai Nagar, Kattankulathur, Kattupakkam, Kazhipattur, Keelkattalai, Kelambakkam, Kilpauk, KK Nagar, Kodambakkam, Kolapakkam, Kolathur, Kottivakkam, Kotturpuram, Kovalam, Kovilambakkam, Kovilanchery, Koyambedu, Kumananchavadi, Kundrathur, Little Mount, Madambakkam, Madhavaram, Madipakkam, Maduravoyal, Mahabalipuram, Mambakkam, Manapakkam, Mandaveli, Mangadu, Mannivakkam, Maraimalai Nagar, Medavakkam, Meenambakkam, Mogappair, Moolakadai, Moulivakkam, Mount Road, MRC Nagar, Mudichur, Mugalivakkam, Muttukadu, Mylapore, Nandambakkam, Nandanam, Nanganallur, Nanmangalam, Narayanapuram, Navalur, Neelankarai, Nesapakkam, Nolambur, Nungambakkam, OMR, Oragadam, Ottiyambakkam, Padappai, Padi, Padur, Palavakkam, Pallavan Salai, Pallavaram, Pallikaranai, Pammal, Parangimalai, Paruthipattu, Pazhavanthangal, Perambur, Perumbakkam, Perungudi, Polichalur, Pondy Bazaar, Ponmar, Poonamallee, Porur, Pudupakkam, Pudupet, Purasaiwakkam, Puzhuthivakkam, RA Puram, Rajakilpakkam, Ramapuram, Red Hills, Royapettah, Saidapet, Saidapet East, Saligramam, Sanatorium, Santhome, Santhosapuram, Selaiyur, Sembakkam, Semmanjeri, Shenoy Nagar, Sholinganallur, Singaperumal Koil, Siruseri, Sithalapakkam, Srinivasa Nagar, St Thomas Mount, T Nagar, Tambaram, Tambaram East, Taramani, Teynampet, Thalambur, Thirumangalam, Thirumazhisai, Thiruneermalai, Thiruvallur, Thiruvanmiyur, Thiruverkadu, Thiruvottiyur, Thoraipakkam, Thousand Light, Tidel Park, Tiruvallur, Triplicane, TTK Road, Ullagaram, Urapakkam, Uthandi, Vadapalani, Vadapalani East, Valasaravakkam, Vallalar Nagar, Valluvar Kottam, Vanagaram, Vandalur, Vasanta Nagar, Velachery, Vengaivasal, Vepery, Vettuvankeni, Vijaya Nagar, Villivakkam, Virugambakkam, West Mambalam, West Saidapet
FITA Velachery or T Nagar or Thoraipakkam OMR or Anna Nagar or Tambaram or Porur or Pallikaranai branch is just few kilometre away from your location. If you need the best training in Chennai, driving a couple of extra kilometres is worth it!
© 2024 FITA. All rights Reserved.